Vulnerability Scan with Snyk MCP Server and Google Code Assist
Ensuring your open-source dependencies are free of security vulnerabilities is a crucial step in modern software development. With the combination of Snyk MCP Server and Google Code Assist, you can now perform quick, AI-assisted vulnerability scans directly within your development environment.
🧰 Prerequisites
Before you begin, make sure you have:
- VS Code installed
- Google Account for Google Code Assist and Synk
⚙️ Setup Steps
-
Install Google Code Assist on VSCode Open the VS Code Marketplace and search for Google Code Assist extension or click the extension icon on VSCode and search Google Code Assist. Click Install and reload your editor once the setup is complete.
-
Add the settings file Inside your repository, create the following configuration file:
mkdir .gemini
touch .gemini/settings.json
settings.json
{
"mcpServers": {
"Snyk": {
"command": "npx",
"args": ["-y", "snyk@latest", "mcp", "-t", "stdio"],
"env": {}
}
}
}
This file will help Google Code Assist interact with your project’s context and external tools like Snyk MCP Server.
- Run the Vulnerability Scan Open the Google Code Assist panel in VSCode and enter the following prompt:
Tell me about any vulnerabilities found in my open source dependencies for this project
Then you will need to accept to use Snyk MCP server.
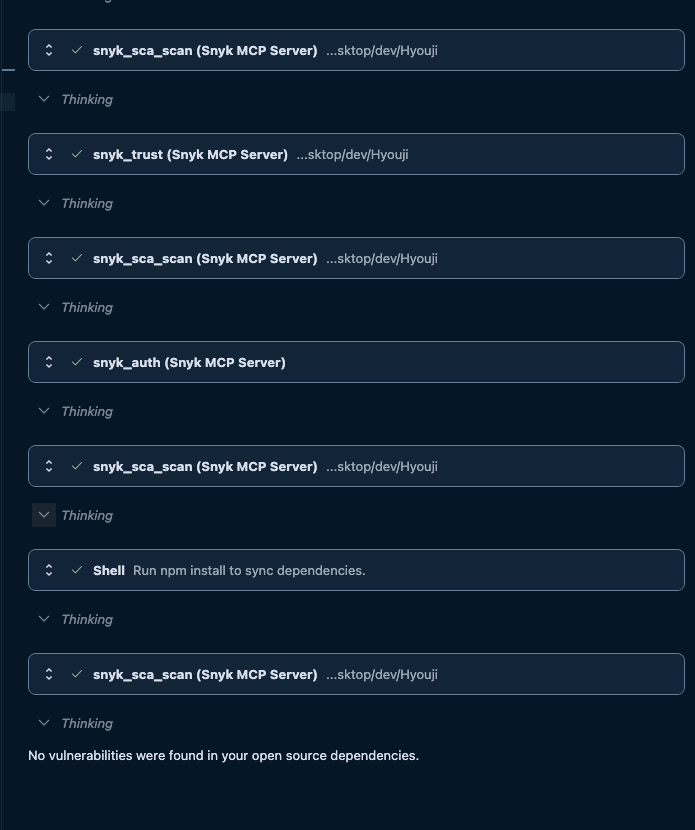
Tried the same prompt with https://github.com/forem/forem
result
I found 48 vulnerabilities in your open source dependencies. Here is a summary of the findings:
Severity Count
Critical 1
High 19
Medium 13
Low 4
Here is a list of the vulnerabilities found:
Package Version Severity Title Remediation
actioncable 7.0.8.7 medium Information Exposure Upgrade to rails@7.1.0
activerecord 7.0.8.7 medium Improper Neutralization Upgrade to active_record_union@1.4.0
activestorage 7.0.8.7 critical Arbitrary Command Injection Upgrade to rails@7.1.5.2
cgi 0.3.6 medium Allocation of Resources Without Limits or Throttling Upgrade to cgi@0.3.7
cgi 0.3.6 medium Regular Expression Denial of Service (ReDoS) Upgrade to cgi@0.3.7
net-imap 0.4.10 high Memory Allocation with Excessive Size Value Upgrade to ahoy_email@2.3.0
net-imap 0.4.10 high Denial of Service (DoS) Upgrade to ahoy_email@2.3.0
nokogiri 1.16.5-x86_64-linux high Stack-based Buffer Overflow Upgrade to nokogiri@1.18.9
nokogiri 1.16.5-x86_64-linux high Expired Pointer Dereference Upgrade to nokogiri@1.18.9
nokogiri 1.16.5-x86_64-linux high Expired Pointer Dereference Upgrade to nokogiri@1.18.9
nokogiri 1.16.5-x86_64-linux low Stack-based Buffer Overflow Upgrade to nokogiri@1.18.9
nokogiri 1.16.5-x86_64-linux high Out-of-bounds Read Upgrade to nokogiri@1.18.9
nokogiri 1.16.5-x86_64-linux low Cross-site Scripting (XSS) Upgrade to nokogiri@1.16.8
nokogiri 1.16.5-x86_64-linux high Stack-based Buffer Overflow Upgrade to nokogiri@1.18.3
nokogiri 1.16.5-x86_64-linux high Use After Free Upgrade to nokogiri@1.18.3
nokogiri 1.16.5-x86_64-linux medium Use After Free Upgrade to nokogiri@1.18.4
nokogiri 1.16.5-x86_64-linux medium Use After Free Upgrade to nokogiri@1.18.4
nokogiri 1.16.5-x86_64-linux low Buffer Under-read Upgrade to nokogiri@1.18.8
rack 2.2.10 high Allocation of Resources Without Limits or Throttling No remediation advice available
rack 2.2.10 low Race Condition No remediation advice available
rack 2.2.10 medium Web Cache Poisoning No remediation advice available
rack 2.2.10 high Allocation of Resources Without Limits or Throttling No remediation advice available
rack 2.2.10 high Allocation of Resources Without Limits or Throttling No remediation advice available
rack 2.2.10 high Allocation of Resources Without Limits or Throttling No remediation advice available
rack 2.2.10 high Allocation of Resources Without Limits or Throttling No remediation advice available
rack 2.2.10 medium Information Exposure No remediation advice available
rack 2.2.10 high Allocation of Resources Without Limits or Throttling No remediation advice available
rack 2.2.10 high Improper Output Neutralization for Logs No remediation advice available
rack 2.2.10 medium Improper Output Neutralization for Logs No remediation advice available
rack 2.2.10 high Relative Path Traversal No remediation advice available
ransack 3.2.1 high Insecure Defaults Upgrade to ransack@4.0.0
rexml 3.4.0 medium Improper Restriction of Recursive Entity References in DTDs ('XML Entity Expansion') Upgrade to rubocop@1.63.5
thor 1.3.1 high OS Command Injection Upgrade to bundler-audit@0.9.2
uri 0.13.0 medium Improper Removal of Sensitive Information Before Storage or Transfer No remediation advice available
uri 0.13.0 low Improper Removal of Sensitive Information Before Storage or Transfer No remediation advice available
@babel/helpers 7.23.6 medium Regular Expression Denial of Service (ReDoS) Your dependencies are out of date, otherwise you would be using a newer @babel/helpers than @babel/helpers@7.23.6. Try relocking your lockfile or deleting node_modules and reinstalling your dependencies. If the problem persists, one of your dependencies may be bundling outdated modules.
@babel/runtime 7.20.13 medium Regular Expression Denial of Service (ReDoS) Your dependencies are out of date, otherwise you would be using a newer @babel/runtime than @babel/runtime@7.20.13. Try relocking your lockfile or deleting node_modules and reinstalling your dependencies. If the problem persists, one of your dependencies may be bundling outdated modules.
brace-expansion 2.0.1 low Regular Expression Denial of Service (ReDoS) Your dependencies are out of date, otherwise you would be using a newer brace-expansion than brace-expansion@2.0.1. Try relocking your lockfile or deleting node_modules and reinstalling your dependencies. If the problem persists, one of your dependencies may be bundling outdated modules.
braces 3.0.2 high Excessive Platform Resource Consumption within a Loop Your dependencies are out of date, otherwise you would be using a newer braces than braces@3.0.2. Try relocking your lockfile or deleting node_modules and reinstalling your dependencies. If the problem persists, one of your dependencies may be bundling outdated modules.
cross-spawn 7.0.3 high Regular Expression Denial of Service (ReDoS) Your dependencies are out of date, otherwise you would be using a newer cross-spawn than cross-spawn@7.0.3. Try relocking your lockfile or deleting node_modules and reinstalling your dependencies. If the problem persists, one of your dependencies may be bundling outdated modules.
inflight 1.0.6 medium Missing Release of Resource after Effective Lifetime Upgrade to canvas@3.0.0
ip 2.0.0 high Server-side Request Forgery (SSRF) Your dependencies are out of date, otherwise you would be using a newer ip than ip@2.0.0. Try relocking your lockfile or deleting node_modules and reinstalling your dependencies. If the problem persists, one of your dependencies may be bundling outdated modules.
ip 2.0.0 high Server-side Request Forgery (SSRF) Your dependencies are out of date, otherwise you would be using a newer ip than ip@2.0.0. Try relocking your lockfile or deleting node_modules and reinstalling your dependencies. If the problem persists, one of your dependencies may be bundling outdated modules.
ip 2.0.0 high Server-side Request Forgery (SSRF) Your dependencies are out of date, otherwise you would be using a newer ip than ip@2.0.0. Try relocking your lockfile or deleting node_modules and reinstalling your dependencies. If the problem.
ip 2.0.0 medium Server-Side Request Forgery (SSRF) Your dependencies are out of date, otherwise you would be using a newer ip than ip@2.0.0. Try relocking your lockfile or deleting node_modules and reinstalling your dependencies. If the problem persists, one of your dependencies may be bundling outdated modules.
micromatch 4.0.5 medium Inefficient Regular Expression Complexity Your dependencies are out of date, otherwise you would be using a newer micromatch than micromatch@4.0.5. Try relocking your lockfile or deleting node_modules and reinstalling your dependencies. If the problem persists, one of your dependencies may be bundling outdated modules.
nanoid 3.3.7 medium Improper Input Validation Your dependencies are out of date, otherwise you would be using a newer nanoid than nanoid@3.3.7. Try relocking your lockfile or deleting node_modules and reinstalling your dependencies. If the problem persists, one of your dependencies may be bundling outdated modules.
tar 6.2.0 medium Uncontrolled Resource Consumption ('Resource Exhaustion') Your dependencies are out of date, otherwise you would be using a newer tar than tar@6.2.0. Try relocking your lockfile or deleting node_modules and reinstalling your dependencies. If the problem persists, one of your dependencies may be bundling outdated modules.
I can also open a Snyk learn lesson for some of these vulnerabilities. Would you like me to open a lesson for any of the vulnerabilities?
